Cybersecurity for Law Firms: How to Prevent and Respond to a Data Breach
Aaron Weismann

Cybersecurity for law firms has never been more critical. Cybercriminals exploit heavily regulated professions and data to blackmail victims and extract substantial ransoms. This is especially true for attorneys, whose careers and licensure depend on preserving confidential clients’ data.
Unfortunately, 1.5 million members of the American Bar Association (ABA) now know what it feels like to have their confidential data breached. In March 2023, these lawyers saw their personal data leaked in a major cyberattack of the ABA website. Just last year, two-thirds of businesses were the victim of a cyberattack.
Attacks are so common that it’s a matter of when and not if you’ll be the victim of a cyberattack. Lawyers need to be prepared. This article covers why cybercriminals are targeting law firms for cyberattacks and provides some tips and tricks for preventing and responding to data breaches.
Why Law Firms Are Prime Targets
Cybercriminals are targeting law firms with cyberattacks because lawyers are heavily incentivized to pay ransoms. Law firms hold large swaths of sensitive information, including information relating to the representation of clients, confidential clients’ information, and other notes and work product.
Unlike other heavily regulated industries, like education, defense, healthcare, and finance, attorneys are personally invested in preventing unauthorized access to information they maintain on behalf of clients.
In law practice, inadvertent or unauthorized disclosure of client information can compromise the client’s posture in litigation. It can prevent a client from claiming privilege of confidential client information or asserting attorney work product protections. This can result in the nonretractable disclosure of that information to opposing counsel.
Ultimately, such disclosures can expose the law firm to organizational sanction. The attorneys involved can also be fined, suspended, or even disbarred for breaches of attorney-client confidentiality and privilege.
Lawyers Have Ethical Responsibilities
The American Bar Association outlined the duties an attorney has to mitigate data security risks in 2018. Formal Opinion 483, titled “Lawyers’ Obligations After an Electronic Data Breach or Cyberattack,” provides detailed guidance about ethical responsibilities related to a data breach or cyberattack.
Competence
Formal Opinion 483’s analysis begins with a bold contention: failure to mitigate data security risks violates Rule 1.1 of the Model Rules of Professional Conduct. Put differently, attorneys lack competence if they can’t protect their confidential clients’ data. They need to “understand technologies that are being used to deliver legal services to their clients” and be able to maintain the proper operation of those tools to prevent security incidents.
Protective Measures
Formal Opinion 483 continues that competence is supported by continuous monitoring to mitigate security risks to clients’ information. Continuous monitoring is demanded by Rules 5.1 and 5.3 of the Model Rules of Professional Conduct and is measured by its reasonableness. Not all cyberattacks will be immediately identifiable, especially not very sophisticated attacks, but the measures to detect attacks must be in place.
Incident Response
Once a security risk or security incident is identified, it needs to be addressed. Formal Opinion 483 explicitly states that the American Bar Association won’t mandate specific actions, but it strongly recommends the imposition of an incident response plan designed to respond to a data breach or cyberattack.
Competence also demands quick restoration of service after a security incident to continue client service under Rule 1.6 of the Model Rules of Professional Conduct. Attorneys must also conduct a forensic analysis to determine the scope and extent of the data breach or cyberattack, similar to inadvertent or unauthorized disclosures of paper documents under Rules 1.4 and 8.4(c) of the Model Rules of Professional Conduct.
Finally, while preserving the confidentiality of clients’ information is paramount, Rule 1.6 of the Model Rules of Professional Conduct only demands reasonableness in doing so. Cyberattacks will happen and lawyers aren’t strictly liable for protecting their clients’ information.
Notifying Clients
Formal Opinion 483 then discusses client notifications of the data breach or cyberattack. If there’s been an inadvertent or unauthorized disclosure, the Model Rules of Professional Conduct demand notification to current clients. Interpretations of the Model Rules of Professional Conduct also require notification to past clients.
Good Data Security Practices
In sum, Formal Opinion 483 provides very reasonable and measured safeguards to protect confidential clients’ data. While it doesn’t provide the mechanisms to do so, it generally encourages following industry-standard good data security practices:
- Know what data you have,
- Understand what’s happening with that data,
- Implement safeguards for that data, and
- Recover operations as quickly as possible.
Cybersecurity for Law Firms 101: Preventing Data Breaches
Preventing data breaches is far from easy, but it’s very straightforward. Remember, you must implement reasonable safeguards to protect and monitor your data. To do so, think about what your environmental topography looks like. Most law offices will have the following:
- An internet connection,
- Some way to parse that internet connection to multiple computers (e.g.: a network switch or wireless router),
- Computers,
- File and email servers,
- eDiscovery and forensic platforms or services,
- Payroll and human resources platforms or services, and
- Cloud storage or services.
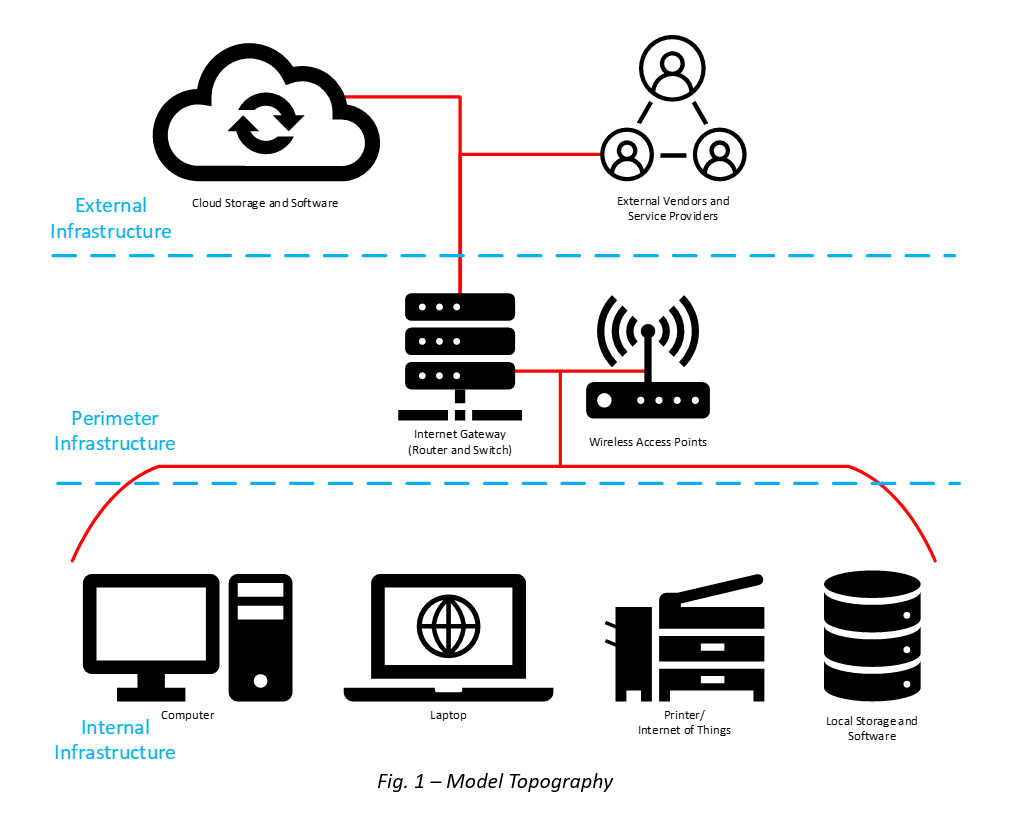
Everything outlined here applies to other infrastructure you may have. If you’re questioning what you should and shouldn’t implement, consider registering for this course to help navigate those decisions.
Monitor Your Firm’s Environment
To protect the confidentiality of your clients’ information and your work product, you’ll need a way to monitor your environment and mitigate attacks. Doing so with your internal infrastructure and perimeter infrastructure means aggregating logs for correlation into a Security Information and Event Management (SIEM) platform. You can supplement that in your managed cloud environment with cloud visibility and monitoring tools.
Protect Communications and Hardware
Protecting communications is also key. Implementing a Secure Email Gateway (SEG) or other communication protection is a must. Those products typically protect incoming email and browser-based attacks, reduce spam in user inboxes, and encrypt outgoing emails. You can learn more about communication security here and email threat mitigation here.
Computers, laptops, and servers can also be protected with defense and response tools. There are a few flavors of this, including:
- Endpoint Detection and Response (EDR), which has supplemented traditional antivirus,
- Managed Detection and Response (MDR), which is EDR with managed services, and
- Extended Detection and Response (XDR), which can include SEG and SIEM-like functionality.
Implement an Incident Response Plan
Finally, you need to implement and practice an incident response plan. Understand how you’ll respond to and recover from an attack, what steps you’ll take for recovery, and which assets are the most critical for recovery objectives.
Practicing that process is critical for two reasons. First, you don’t want the first time you execute your plan to be during an incident. That will delay your recovery and you could discover that you didn’t cover critical resources in the plan.
Second, you need to make sure your recovery works as planned. If, for example, you make backups of critical files and sensitive data, the last thing you want to discover during recovery is that those files weren’t successfully backed up.
Consider Cyber Liability Insurance
Part of your incident response plan should include cyber liability insurance. Incident recovery, client notifications, and potential regulatory compliance can be very expensive. Companies have been bankrupted just by response efforts. Having adequate cyber liability insurance can help offset those costs and others and preserve business operations.
Cybersecurity for Law Firms 102: Responding to a Breach
Law firms must assume that a cyberattack is a matter of when - not if - and plan for the inevitable. So how do you respond to a data breach or cyberattack?
- Confirm the attack. This might seem obvious, but you’ll want to use your early warning and detection systems to confirm an attack is happening.
- Identify the blast radius. Figure out what’s been attacked and if the attacker is still in your systems. You’ll also want to identify whether data was exfiltrated and stolen.
- Stop the attack. Cut the attacker off and halt the progress of the attack and theft of data. Consider shutting down systems or cutting off internet connections. Decisive action at this point can avert substantial damage.
- Recover. Implement your incident response plan to recover data and operations quickly.
- Notify impacted parties. You’ll determine what notifications should be made and make those notifications. Remember, Formal Opinion 483 states that the purpose of this notification is so the client can make an informed decision about continued representation.
- Comply with privacy and security laws. Depending on the nature and contents of the information stolen or viewed by a cybercriminal, you may need to comply with state and federal law during the mitigation, restoration of services, and notification. Make sure to evaluate your exposure.
- Comply with ethical rules. Ethics rules allow you to make certain disclosures to law enforcement and to recover from an attack. You’ll also need to work through the guidance outlined in Formal Opinion 483 to guide your recovery efforts. There may also be state ethics decisions applicable to your situation.
Conclusion
Cybersecurity for law firms and lawyers is both critical and tricky to implement. Navigating ethics and managing both your operations and clients can pose a unique and extraordinary set of challenges. To make matters worse, the legal industry is a prime target for cybercriminals.
By implementing reasonable and industry-standard protections and following guidance provided by ethical oversight organizations, you’re on solid footing to recover and continue operations.

Aaron Weismann is the Chief Information Security Officer at Main Line Health, a health system serving the Greater Philladelphia Area. Prior to that he worked for the Commonwealth of Massachusetts both as a CISO and as an IT contracting, security, and privacy attorney. He was also an attorney at State Street Bank and Trust Company. Aaron received his Juris Doctorate from Washington University in St. Louis in 2009 and an LL.M in Global Law and Technology, Intellectual Property and Information Technology Law Concentration from Suffolk University in 2010.
This post was written by a guest blogger. Although this article was thoroughly reviewed by NBI staff, the views, opinions and positions expressed within the post are those of the author alone and do not represent those of NBI. The accuracy, completeness and validity of any statements made within the post are not guaranteed. We accept no liability for any errors, omissions or representations.
